1 Introduction
At present, the theft of cars occurs from time to time. The GPS is also used to navigate the vehicles. It only needs to receive more than two of the 24 geostationary satellites (more and more accurate) to display the current vehicle. Location, but it can only receive information without transmitting function, so it has no effect on anti-theft. This device is easy to use, close W1, the owner can leave the car; when returning, disconnect W1. If you are hijacked while driving, just close W2. And the cost is low, and there is no need to pay various alarm fees, which is very suitable for the installation of low-end cars.
2 Working principle
Anyone who is familiar with mobile phones knows that the mobile phone has a positioning function, and can send a prescribed letter to a specific number to get a reply to the text message to inform you of your current location. Of course, it is achieved through the mobile communication network platform.
For mobile communication platforms, the prescribed letter is: ZJ; the specific number is: 05058. When the ZJ letter is sent to 05058, you can get a text message sent back from the mobile communication network to inform you of your current location. This kind of position information is usually in the form of polar coordinates (Ï, θ), which is based on a famous building nearby as the pole, and then the distance between your current position and the pole is the vector Ï, and the vector Direction θ. How to use the mobile communication network to realize the positioning function of the car? Figure 1 shows the working diagram of the technology.
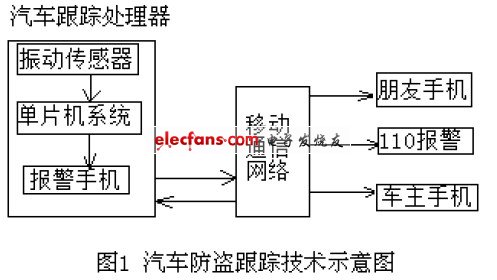
It is a system composed of a car tracking processor, the owner's mobile phone, etc., and then a mobile communication network platform. The core part is a "car tracking processor" installed in the car, which consists of a mobile phone, a single-chip microcomputer, a vibration sensor, and so on. Normally, the sensor does not work. When the owner leaves the car, the sensor starts to work. At this time, if a thief moves the car, the sensor output signal makes the single-chip system work, and sends the ZJ letter to the mobile communication network 05058 through the alarm phone The location information of the car sent back from the network. It is then controlled by the single-chip microcomputer, and the location information is sent to the mobile phone of the owner through the mobile network, which shows that no matter where the owner is, he can know the actual location of the car. When the thief starts the car, the car tracking processor will repeat the previous process at regular intervals (one minute to one and a half minutes), and inform the owner of the current car position one by one, which plays a role of position tracking.
If the owner of the car is hijacked by the thief during the driving process, only a small, inconspicuous action, and a small hidden switch can be pressed to make the car tracking processor repeat the above process regularly. Of course, the recipient of the location information is not the owner I, but my relatives and friends (if calling for help from 110, it needs to be forwarded by the mobile phone of relatives and friends, because 110 does not yet have the function of receiving SMS)! Let them understand their whereabouts and win the shortest rescue time.
3 Hardware design
The hardware design here refers to the design of the "car tracking processor", the main part of which is the single-chip system. Figure 2 shows the hardware design diagram. The single chip microcomputer adopts the most popular and cheapest small volume (20 feet) AT89C2051.
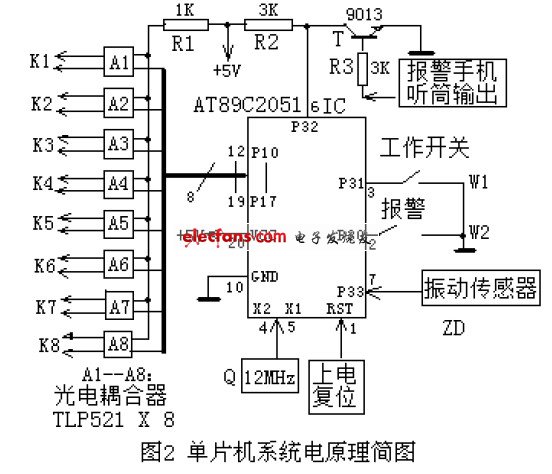
When the owner leaves the car, the work switch W1 should be closed. When the owner is hijacked, the hijacking alarm W2 should be closed. These two switches should be installed in a place that is relatively concealed but easy to reach with your hands. The eight pins of the P1 port (P10-P17) of the AT89C2051 are used to control the turning on and off of the eight photocouplers A1—A8 (the pins are turned on when the level is low). Isolation, because the level of the mobile phone keyboard is not the same as the level of the single-chip system. When the single chip microcomputer system is initialized, all input and output pins (P10—P17, P30—P33, etc.) are at high level. When the vibration sensor does not work, it outputs a high level, and the single-chip microcomputer does not work; when the car is stolen, the sensor outputs a low level, which triggers the single-chip microcomputer to work. Controlling A1—A8 through P10—P17 causes K1—K8 to be turned on and off respectively, simulating a series of key actions of the alarm mobile phone, and completing the entire alarm process.
The handset of the alarm phone must be disconnected to prevent the car thief from hearing it. But its output signal must also be retained, and input it to R3, 9013, as a prompt signal for the mobile communication network to send back location information. The P32 pin of the IC was originally high, and when prompted, it becomes low, so the microcontroller controls the alarm mobile phone to send the location information (the owner's mobile phone, friend's mobile phone or forwarding 110, etc.).
Although the alarm phone has 19 keys, we only use 8. See the keys labeled K1-K8 in Figure 3, and each key is connected to the corresponding two wires. Because the alarm mobile phone can adopt many styles, the specific keyboard arrangement and the function of each key are different. It should be treated differently when using it. Of course, the programming of the program is also different. This should be especially noted. The mobile phone we use is the cheapest mobile phone (Bird_BiRD_S1160). The mobile phone itself does not require any money, just pay 500 yuan for the phone bill. Each key of the mobile phone has multiple functions, such as K1 can send and send text messages, etc .; K2 can enter the preset phone book; K3 can shut down, reverse, etc .; K4, K5 can turn up and down; K7, K8 can type "ZJ" letters and so on. Due to space limitations, it can not be exhaustive, please refer to BiRD_S1160 instruction manual.
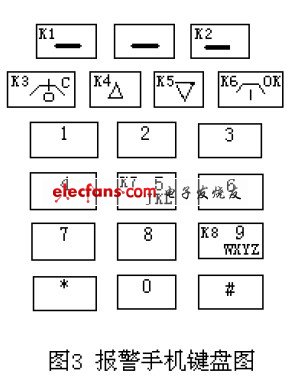
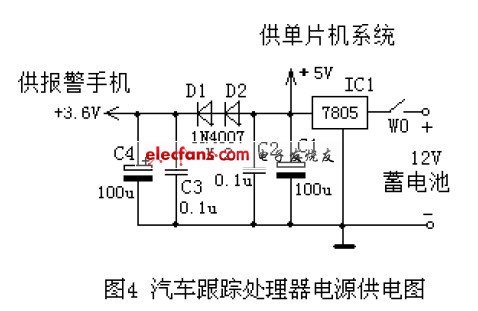
Figure 4 shows the power supply diagram of the car tracking processor. It is supplied by the storage battery of the car after two voltage drops, and the voltage is reduced from 7805 to 5V for the single-chip system, and then the two diodes are reduced to 3.6V for the alarm mobile phone.
The "vehicle tracking processor" composed of an alarm phone, a single-chip microcomputer, a vibration sensor, a power supply, etc. should be placed in a relatively hidden place inside the car. This connection of the alarm phone does not hinder the original performance and use of the phone. Before using the alarm mobile phone, three phone numbers should be preset in the phone book of the mobile phone in order: 1: the owner's phone, first store the owner's name, then the owner's phone number; 2: location information, first store Chinese Location information ", then store 05058; 3: Alarm call, first store" Save! AX-33445 "(the letters and numbers at the back are the car license number), and then store the friend's phone number. Then you just need to enter the phone book to choose. The function keys of different mobile phones are also different. For details on the use of this mobile phone, please refer to the BiRD_S1160 instruction manual.
Fiber Optic Ip68 Enclosure,Ftta Ip68 Hardened Connections Device,Ftta Ip68 Hardened Connections Fast,Fiber Optic Ip68 Enclosure Adapter
Huizhou Fibercan Industrial Co.Ltd , https://www.fibercannetworks.com